EIM Policy Elements
This topic lists the different elements that you can use in EIM policy documents.
|
EIM policies are case sensitive. All elements must start with an upper-case letter. |
Elements
Statement
| Description | Examples | ||
|---|---|---|---|
The main element, required in every There is one
|
|
Sid
| Description | Examples |
|---|---|
The statement ID ( |
|
Action
| Description | Examples | ||||
|---|---|---|---|---|---|
Specifies one or more actions that are allowed or denied. Every individual statement requires either the To specify an action, you must specify the service followed by a colon, and use the name of an API method (for example
You must use one of the following codes:
This element is an array that contains one or more actions, enclosed in quotation marks and separated by commas. You can use asterisks ( |
|
NotAction
| Description | Examples | ||
|---|---|---|---|
Specifies one or more exceptions to a list of actions. Every individual statement requires either the This element format is the same as the You can use this element to create shorter statements instead of specifying a long list of actions in the
|
|
Effect
| Description | Examples |
|---|---|
Specifies whether the statement explicitly allows ( By default, access to resources is denied until it is explicitly allowed in a policy statement. To enable users to access resources, you must set the |
|
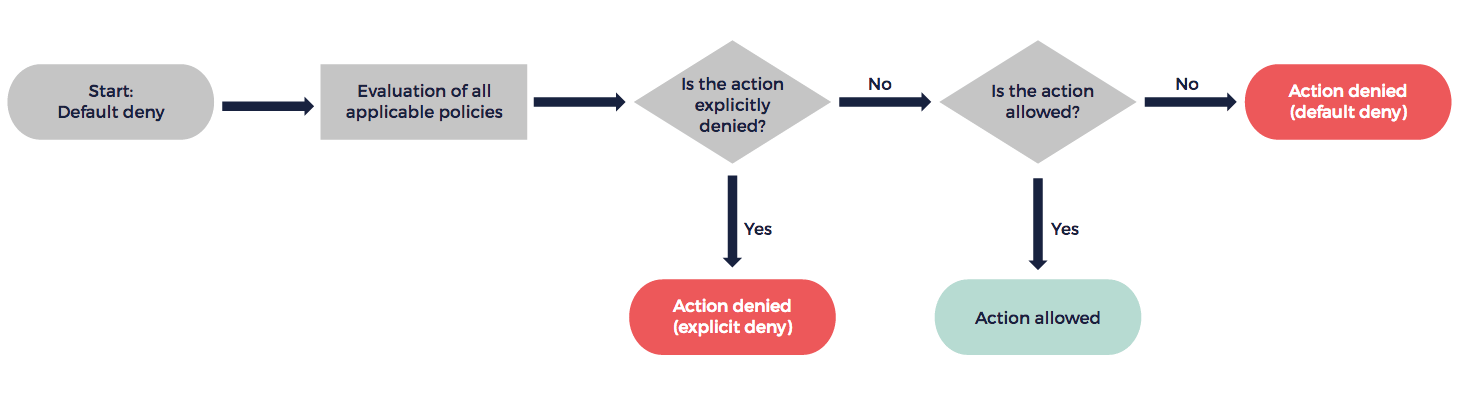
Difference Between Default and Explicit Deny
When a user sends a request, EIM evaluates this request in regards of all applicable inline or managed policies.
If you did not explicitly allow the action contained in the request in a policy statement for this user, the action is denied. This is default deny. However, if you explicitly denied the actions in a policy statement for this user, this action is denied even though another policy statement allows it. This is explicit deny.
In other words, an allow can overrides a default deny, while an explicit deny overrides all allows and cannot be overridden.
The following flow chart shows the process to determine whether the action contained in a request is allowed or denied:
Related Pages
AWS™ and Amazon Web Services™ are trademarks of Amazon Technologies, Inc or its affiliates in the United States and/or other countries.